The company later said it was a testing playground, raising doubts in its statement.
Several internal databases, passwords and secret access keys to internal Nokia systems were left unattended on a leaky etcd server. Credentials included Heketi user and admin passwords, a Redis password, a Weave password, a k8s secret encryption key, a Gluster user private key, SSH and RSA private keys, a cluster key, AWS S3 secret keys and a couple of others. Additionally, a log server was running on another port with the same IP that had no authentication enabled.
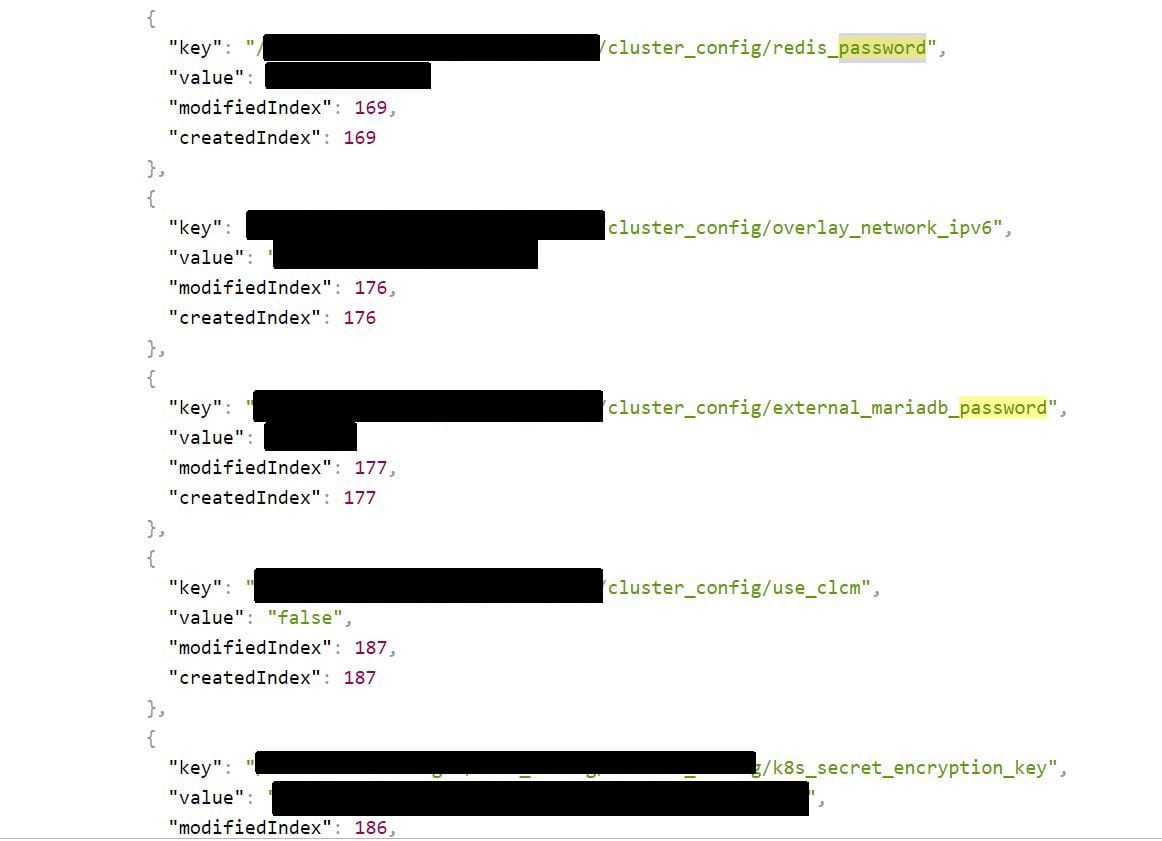
We have identified data during our regular Shodan security audit on Dec 13th. Upon this discovery, we immediately contacted the Nokia Security team via our specially designed “Responsible Disclosure” form on their website.
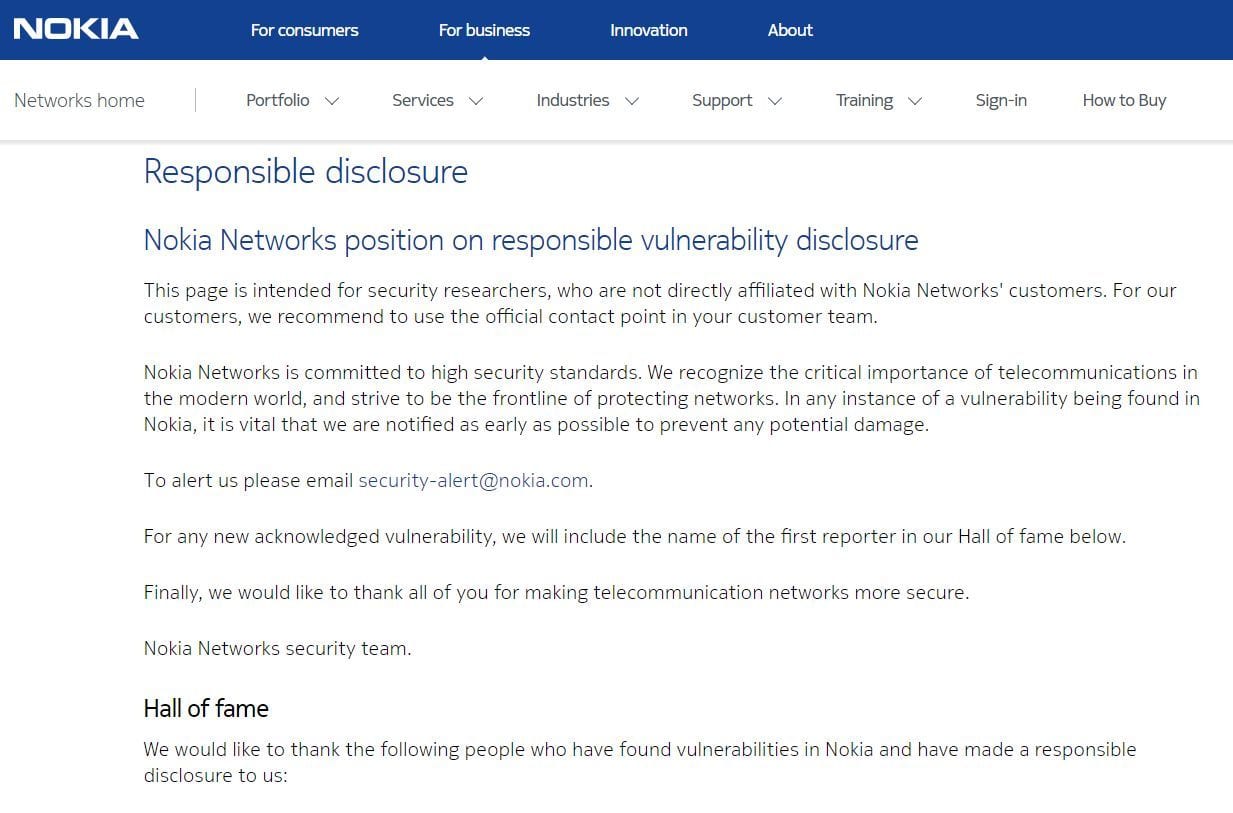
There was no response for more than 24 hours, so Bob Diachenko, director of the cyber risk research team at Hacken.io and Hackenproof.com tried to find a relevant contact on Twitter. Finally, on Monday, Dec 17th the data was taken offline and the system fully secured, with confirmation sent on behalf of the Nokia Security team. The company stated that it was a testing environment:
“This particular AWS server was created some time ago by one of our developers for testing purposes. We can confirm that the server contains no sensitive information. That said, we’ll use this episode for own awareness training for Nokia R&D employees”.
Although it is unknown if any customer data was put at risk (as systems observed were mostly of industrial nature), there is still a great danger of these credentials being exposed on an unprotected public server online, indexed by an IoT search engine. At the end of the day, we can not be 100% sure that this was a testing data, given the nature of the observed environment and the number of exposed passwords. It is also important to note that we did not try to use credentials against the services.
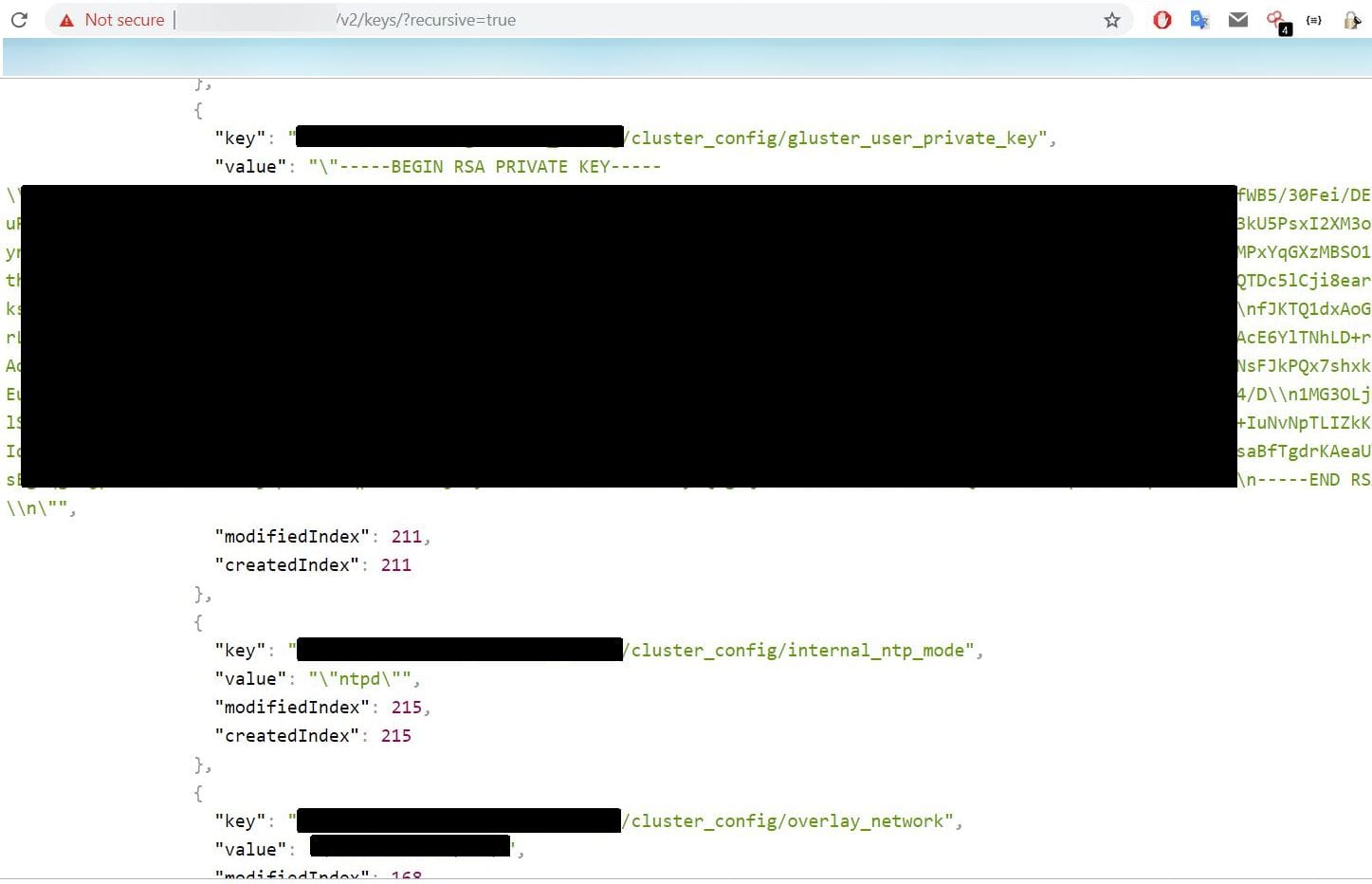
Back in March this year it was reported that more than 2,000 leaky etcd had been seen online. This number seems to have remained at the same level (2,519 instances indexed by Shodan as of Dec 2018).
Similar to other databases and systems, etcd servers shouldn’t be exposed on the Internet, and admins should change their default settings so the servers pass credentials only when users authenticate themselves.
Etcd is a type of database that computing clusters and other types of networks use to store and distribute passwords and configuration settings needed by various servers and applications. Etcd comes with a programming interface that responds to simple queries that by default return administrative login credentials without first requiring authentication.
How Hacken can help
At Hacken, we take security extremely seriously, and all the checks are performed according to the highest standards. If you have any questions about the topic or need a consultation, feel free to contact our Team!

