On the 21st of December 2018, while researching another output of Shodan search results, we discovered an unprotected Elasticsearch cluster exposing millions of records with very sensitive data.
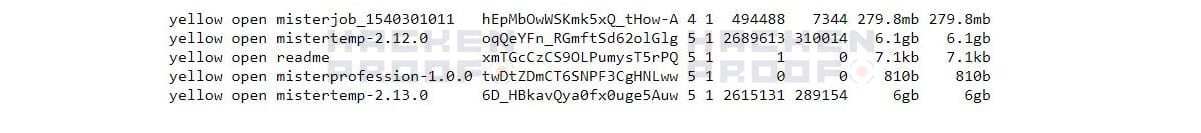
The names of the indexes and their content left no doubt as to the owner of data – an “online temp agency” known as MisterTemp – which claims to be a place where anyone can quickly apply for a temporary job and offers “temporary assignments throughout France” in a variety of sectors.
A quick search on related names showed at least 2 IPs were exposed, with passwordless Elasticsearch clusters available for public access:
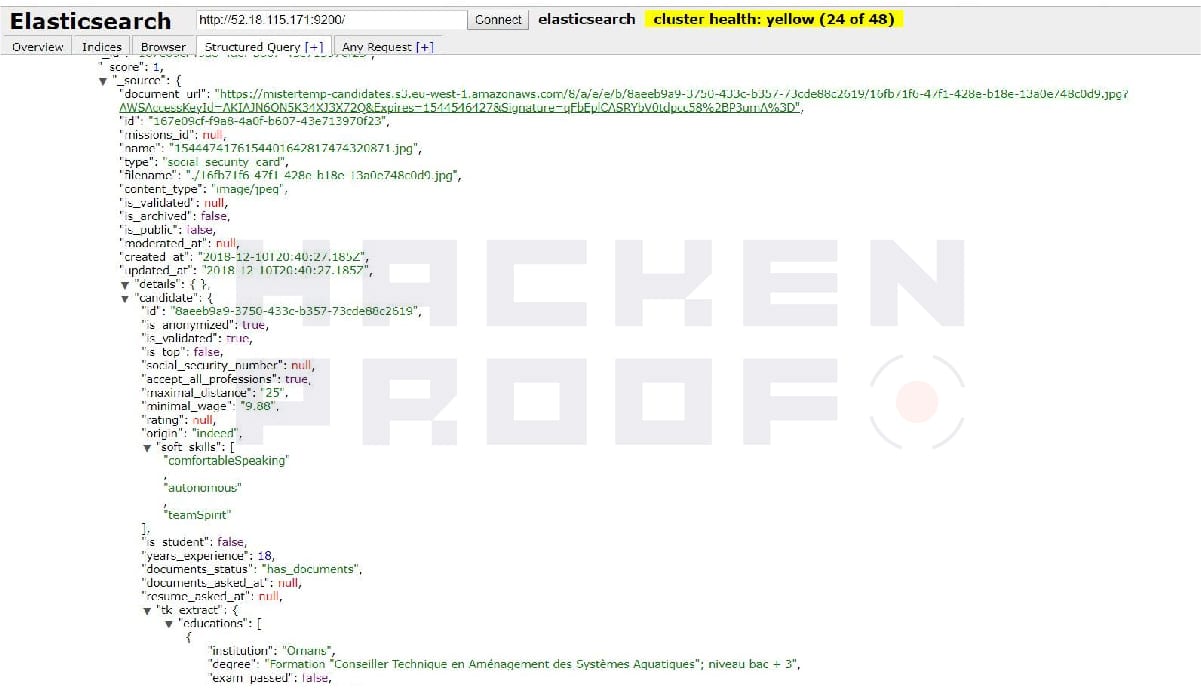
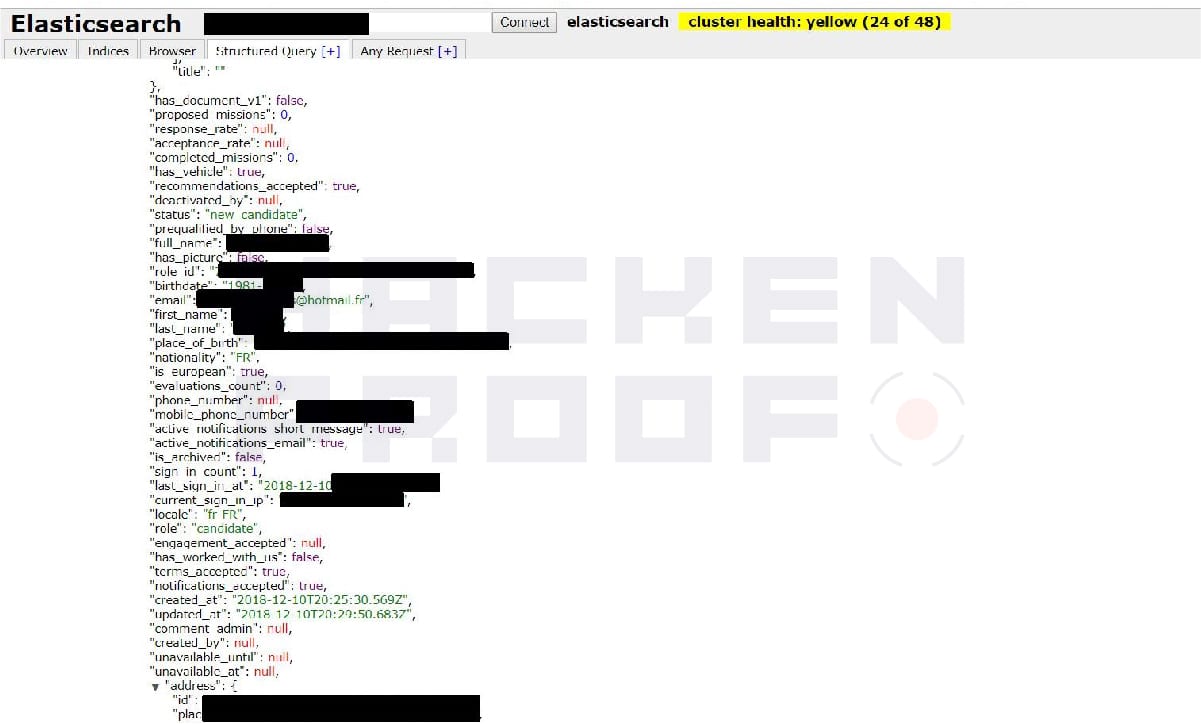
The total number of records in the index called ‘mistertemp-2.14.0‘ was 2,898,153. Each record was structured to represent fairly detailed and sensitive data on the applicants, such as name, email, address, birthdate, nationality, mobile phone number, links to the external S3 storage with resumes and scanned documents, education level, skills, experience, and in some cases – social security cards or passport numbers.
Please note that the number of records can’t represent the number of affected people – we did not analyze each and every document in the storage, but only a sample of data taken for verification purposes only.
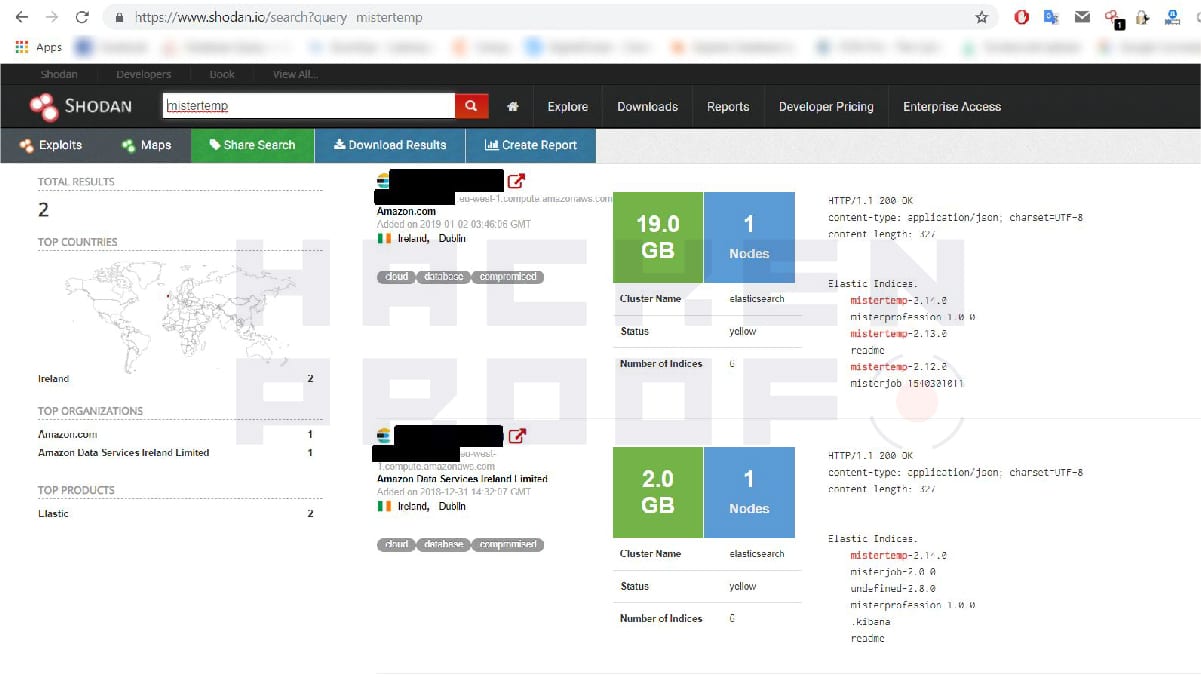
It is worth noting that the exposed instance contained a ‘readme‘ file which is usually left by malicious actors who scan the Internet for unprotected databases with sensitive data, delete the data, and ask for a Bitcoin ransom:
On the 21st of December, we immediately sent a private security notification alert to the various emails of MisterTemp’s contact persons. The only response we received was an automated holiday reply. We repeatedly sent more notifications on Dec. 28th and after the New Year holiday, including notification sent to CERT-FR, after which we requested assistance from a local security researcher at ZATAZ and Damien Bancal.
On Jan 9th, 2019, Damien was able to connect with MisterTemp’s senior management over the phone and urged them to secure the unprotected Elasticsearch instance (which has continued to update in real-time with more applications). On the same date, the database was taken offline and is now no longer available.
During a follow up with us, a representative of MisterTemp thanked us for the discovery and report, blaming human error for the exposure of the database. It is unknown whether the company plans to alert its applicants on the breach.
The danger of Open Elasticsearch Instances
We have previously reported that a lack of authentication allows for the installation of malware or ransomware on Elasticsearch servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
To learn how you can minimize the risks of your cloud infrastructure becoming exposed – contact us for a free consult.

