Today we are going to dig into the source code of everiToken, a token-based blockchain program on HackenProof. We will introduce its concept and technical details, show how to set up the node, and run some test requests to the API. We’ve also included a vulnerability description of a bug found in everiToken’s node.
everiToken introduction
Supported by world-renowned investors such as Fenbushi Capital, everiToken is the world’s first token-based public chain. Switzerland-based everiToken delivers up to 10,000 transactions per second (TPS), robust security, and a high level of standardization. Instead of using a smart contract layer in their public chain structure, everiTokеn has implemented a new technology called a “safe contract.” Both traditional apps and decentralized apps (DApps) can use everiTokеn to conduct issuance, transfer, and management of tokens by calling token-related APIs.
Whitepaper overview
Although everiToken is based on EOS, the everiToken public chain does use some Ethereum concepts. everiTokеn uses “safe contracts” instead of smart contracts, which means that everiTokеn is not Turing complete so it can satisfy a range of complicated application scenarios. The everiToken EvtLink standard is used to generate a QR code for everiPay, the first commercial token payment standard made for face to face micropayments using everiTokеn. Since everiTokеn is based on EOS, it utilizes a Boost.MultiIndex-based memory database (Chainbase) that supports rollback operations.
The infrastructure features two types of tokens: Fungible Tokens and Non-Fungible Tokens. Non-Fungible Tokens (NFT Tokens) are composed of 3 parts – a domain name, a token name, and an owner. NFT Tokens do not have value and can be transferred to other owner or owner groups. Fungible Tokens (Points) can be issued after registering a symbol and setting the number of tokens that will be issued. Anyone with their own private key can transfer their tokens to others.
everiToken uses a token-based transaction model for non-fungible tokens. Its database includes two parts, a Token DB and a Block DB.
everiTokеn uses BFT-DPOS as its consensus algorithm. DPOS has proven capable of meeting the performance requirements of various applications on the blockchain. Under this algorithm, those who hold EVT tokens may select block producers through a continuous approval voting system.
EVT is the fuel used by everiTokеn. A small amount of EVT will be added to every operation as a service fee, which will then be sent on to the transaction producer as a reward. The number of EVT charged will float automatically, and the fees collected are primarily to prevent malicious attacks and will not affect most users’ regular use. For additional information, please review the everiToken documentation. It may help our readers better understand the procedures described below.
Node installation
Before deploying the node you need to install the Docker.
Pull the image from the repository:
docker pull everitoken/evt:latest
And start the Everitoken node:
docker run –name evtd -p 8888:8888 -p 9876:9876 -t everitoken/evt evtd.sh –http-validate-host=false –charge-free-mode
Call this API to get versions:
curl localhost:8888/v1/chain/get_info
Response:
{
“server_version”:“b2674828”, “chain_id”:“dae43118cc62801c4148c4143865be5bde49561fc61671516fc9183cdec91337”,
“evt_api_version”:“3.1.2”,
“head_block_num”:1,
“last_irreversible_block_num”:0, “last_irreversible_block_id”:“0000000000000000000000000000000000000000000000000000000000000000”,
“head_block_id”:“000000019034e61532475fe9e396442127692fb3ddad3f971714213d5c0b2742”,
“head_block_time”:“2018-05-31T12:00:00”,
“head_block_producer”:“”,
“recent_slots”:“”,
“participation_rate”:0.00000000000000000
}
Testing
In the previous article, we showed you how to “fuzz” an API with a self-written python script. But there is an advanced way to test an API with Burp Suite.
Firstly you need to set up a proxy on your browser. Then turn an interception in Proxy tab and catch a request to your node.
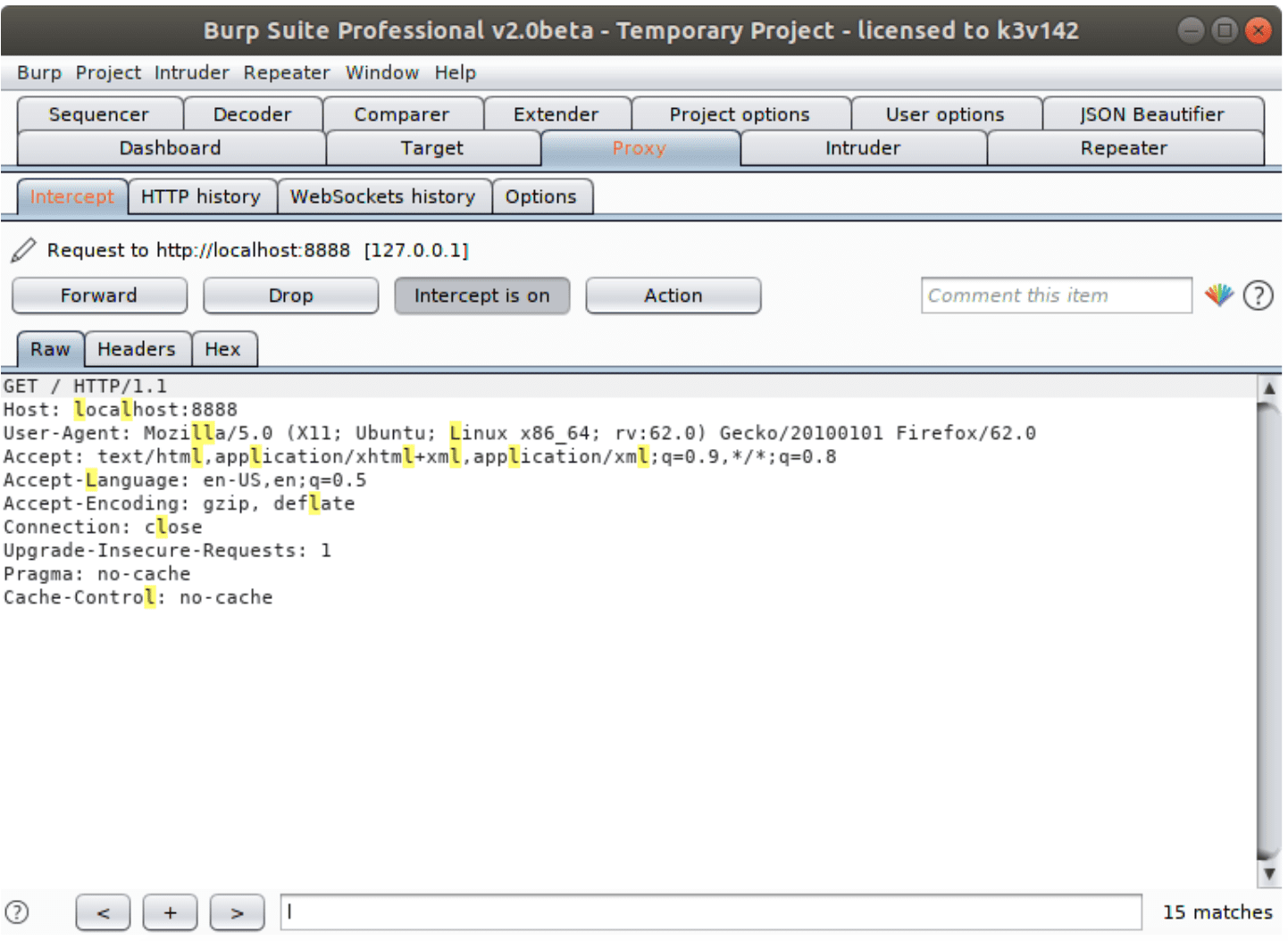
Tap Action button and Send to Intruder. Go to Intruder tab and set the targets you want to test. Select a parameter and click Add.
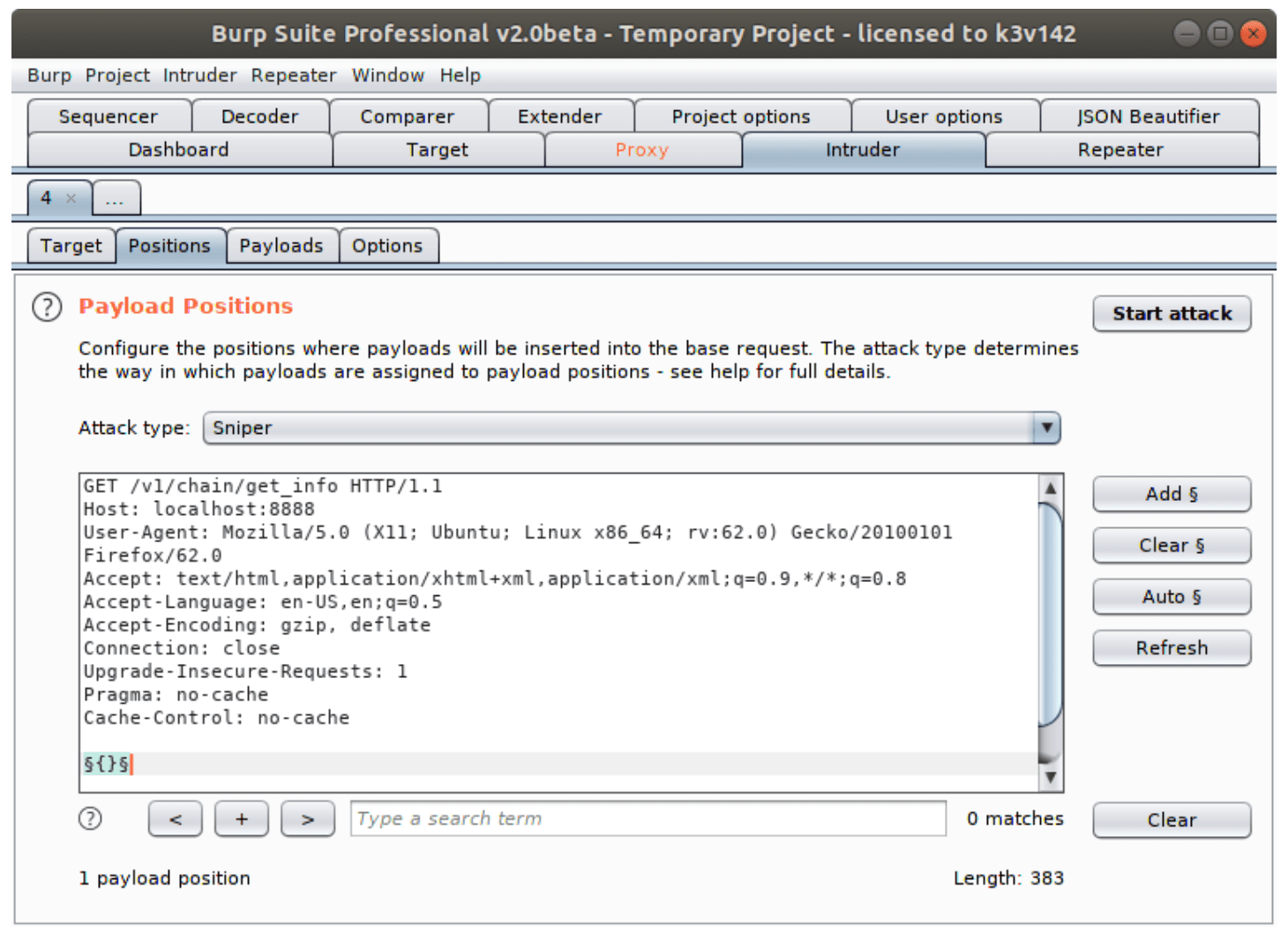
In Payloads tab load your dictionary. I am choosing this one. Click “Start attack” and fuzzing will start. After the script finishes its work you will see the result.
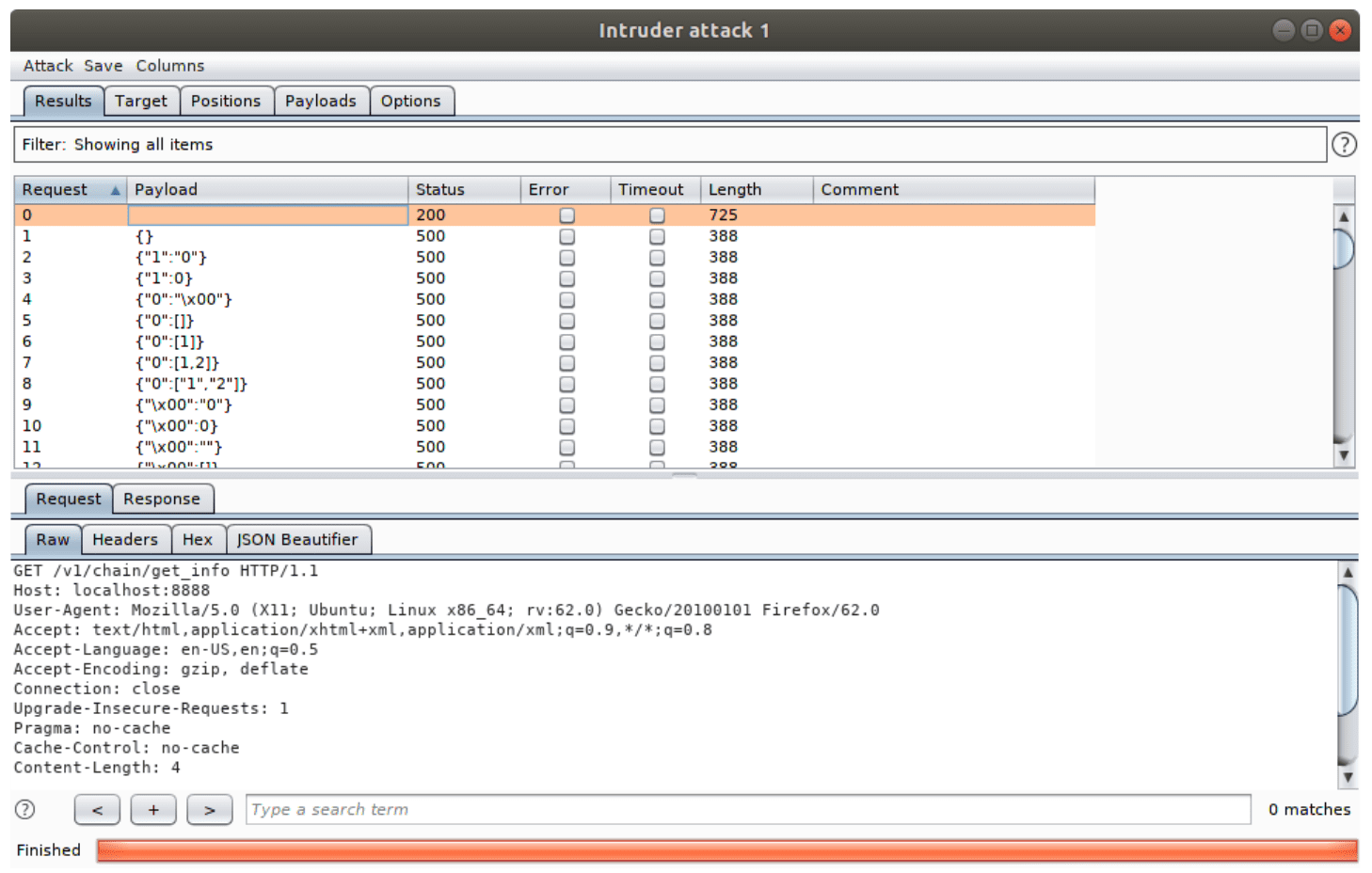
By following this method I’ve found a vulnerability in EVT that allowed me to crash any node in the network.
Report from hackenproof.com
everiToken’s node crashes when non-hex id value is passed in get_transaction function. As far as this API function is accessible remotely without any authorization – any EVT node can be DoSed remotely.
read_only::get_transaction(const get_transaction_params& params) {
auto block = db.fetch_block_by_number(params.block_num);
for(auto& tx : block->transactions) {
if(tx.trx.id() == params.id) {
auto var = fc::variant();
abi_serializer::to_variant(tx.trx, var, make_resolver(this));
return var;
}
}
FC_THROW_EXCEPTION(unknown_transaction_exception, “Cannot find transaction”);
}
As the node doesn’t filter user input, after the request to the database with malicious parameters an exception is raised and the node is crashed.
Conclusion
In this review, we focused on everiToken, the first EOS-based blockchain on hackenproof.com. Switzerland-based everiToken raised $10 million in a private funding round led by Chinese crypto investment giant Fenbushi Capital. everiToken’s award-winning payment solution everiPay boasts a capacity of over 10,000 transactions per second (TPS). Please visit everiToken.io and github.com/everiToken for more information.
Now you know how to install everiToken nodes and how to test them using the Burp Suite. Also, we’ve shown you a real example of the vulnerability that was found in EVT.
HackenProof is constantly publishing “How to hack” posts in order to help researchers test blockchain based products. Please check How to hack VeChainThor and How to hack Smart Contracts.

