Kars4Kids is a charity that asks people to donate their cars, motorcycles, RVs, and real estate. They are most known for their nationwide advertising using their hypnotic theme song where a child and a Johny Cash impersonator sing the phone number and invites people to donate their cars today.
On the 3rd of November, Bob Diachenko, Director of Cyber Risk Research at Hacken has found what appeared to be a publicly accessible MongoDB. Upon further investigation, the data seemed to contain the emails and personal data of 21,612 Kars4Kids donors/customers and super administrator login and password details.
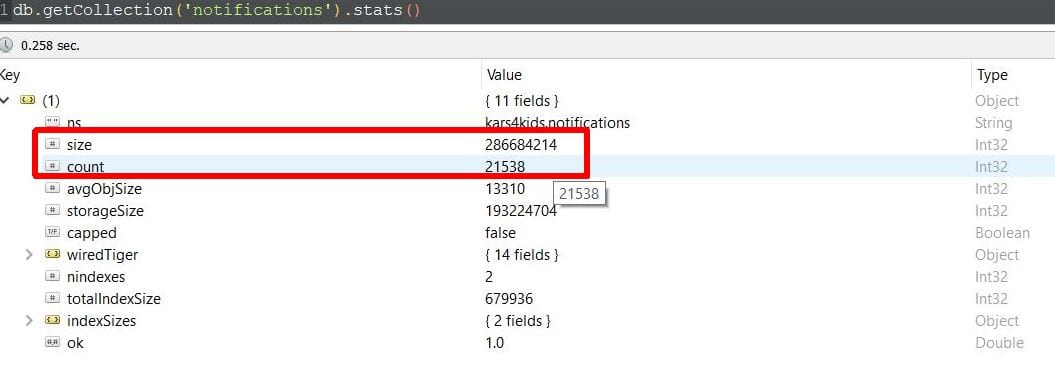
What is worse is that there were internal accounts with usernames and passwords that cybercriminals may have used to access the Kars4Kids dashboard, that would give them access to even more sensitive data – like vacation vouchers (free holidays for those that donated their vehicles) and receipts, with such personal data like emails, home addresses, phone numbers, and etc.
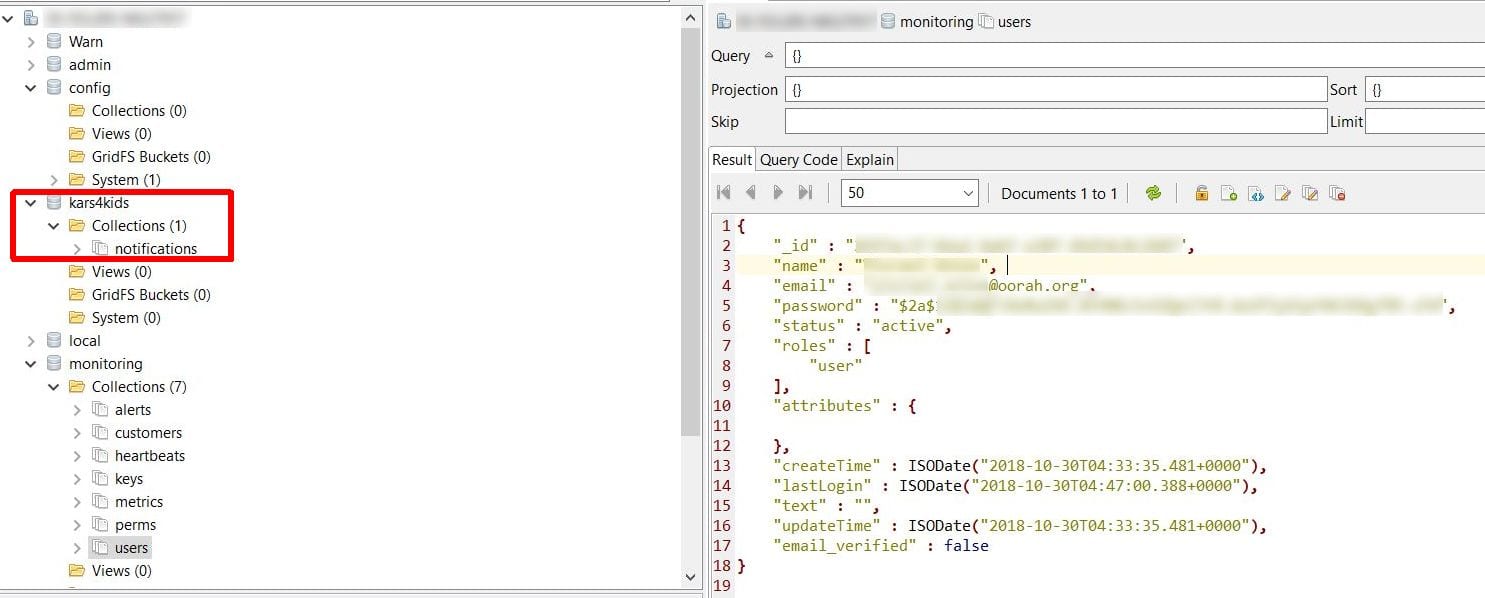
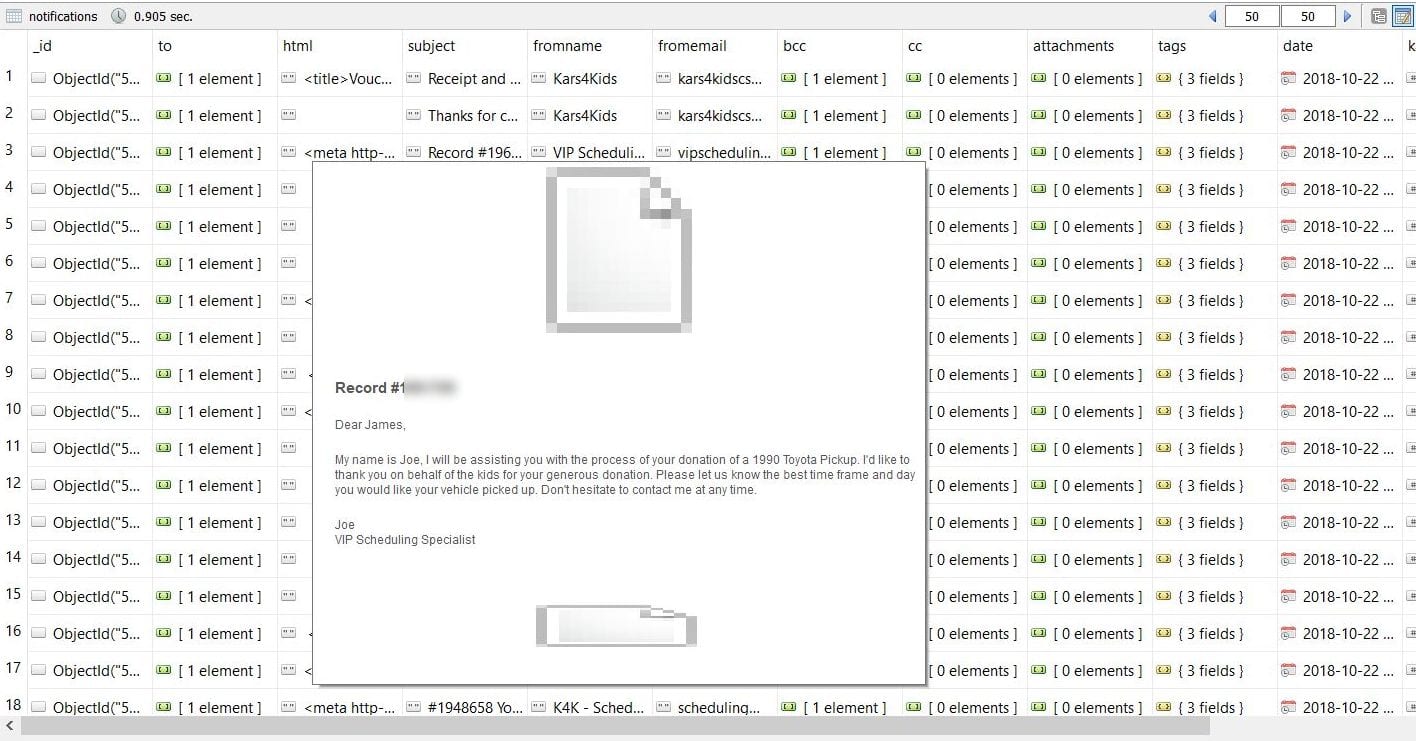
As security researchers never circumvent passwords or access this type of data we can only speculate that cybercriminals could easily log in to accounts or abuse admin privileges.
The Ransom Note
We have seen multiple misconfigured instances of MongoDB where human error makes the database publicly accessible without a password. This means that anyone with an internet connection could have had access to Kars4Kids’ data. In fact, there is clear evidence that cybercriminals placed a ransom note inside their database.
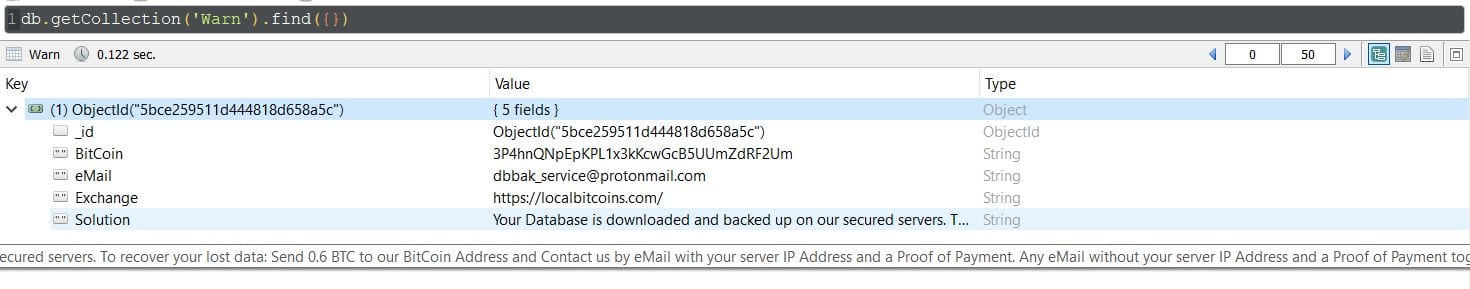
In 2017 three groups of hackers have wiped around 26,000 MongoDB databases and demanded victims to pay about $650 per database on average to have it restored. In total researchers estimate as many as 75,000 databases were affected. This March Bob Diachenko has conducted a test by creating a honeypot database that contained 30GB of fake data. It took only three hours for hackers to identify the database before wiping out its data in just 13 seconds and leaving a ransom note demanding 0.2 Bitcoin.
We cannot confirm or deny that cybercriminals have downloaded the entire Kars4Kids’ database, but the ransom note provides reasonable suspicion that it is a possibility. It is unclear how long the data was exposed or how many others gained have access to it before the notification was sent and ultimately secured.
The Firewall at the Top and Response
On the 3rd of November, a notification email was sent to multiple email addresses with no reply and the database remained open until the evening of November 5th. It took 3 hours by phone to reach someone despite telling the volunteers who answer the phones that this is a serious issue and we need to speak with someone in the IT Technology department or senior management. On one occasion the call was forwarded to someone in Israel who could not give me names, contacts, or emails of anyone who could secure the data and told me to call the same main number again.
We understand that it is a common practice to create a buffer zone between the public and senior managers or leadership. However, the most shocking thing was that an organization or company would not have a data breach or crisis action plan for when a report is made. During the notification process, we told anyone who would listen what happened, how important it is and that we must speak with someone to help secure this data urgently. The issue here is that every organization must understand the value of the information they store and collect. They must take every possible step to secure and protect that data. This includes training everyone to be on the same page and enact a data breach protocol for when the worst happens.
On November 7th we received a reply from a Kars4Kids representative:
“We take the security of our donors’ information extremely seriously. After looking into this matter, we immediately secured the vulnerable database, notified the FBI cyber division, and also informed those donors whose information was affected. Unfortunately, as a nonprofit organization, we do not have a discovery bounty program in place. We do very much appreciate your letting us know of this issue and your dedication to keeping the web secure”.
Controversy
As security researchers, our primary goal is protecting user’s data online and data security education. We report facts and opinions and have no bias in the companies or individuals we report on. Charity is a very honorable cause and we are not implying any wrongdoing by Kars4Kids or their sister company Oorah. However, when researching more closely we discovered that the charity has faced some controversy in the past and we wanted to include that in the report.
The subject of the controversy is the Kars4Kids advertising jingle. The song was recorded in 1999 and has achieved cult status for good or bad. It has been parodied by FOX’s cartoon series Family Guy, used as CIA torture in a SNL skit, and radio host Don Imus was recorded on a “hot mic” telling the charity to “go to hell” over the song.
Questions Remain
Suffering a data breach can happen to anyone and Kars4Kids is not unique in this case. Companies and charities large and small must make sure that they are taking every possible step to secure the data they collect or store. When digging deeper in the publicly accessible database did the pieces of the puzzle start to become more clear on what Kars4Kids actually does or how it looks from the inside.
If your organization requires help on securing their data and want to consult with our experts, you can reach out to us at any time.

