The entities working in the government sector worldwide provide a wide range of services to citizens and corporate players and, thus, process large volumes of sensitive data and corporate secrets. As a result, their systems and networks become lucrative targets for cybercriminals. To ensure effective protection of the information they store, government sector agencies would need to employ a huge cybersecurity staff. However, for the last few years, government sector agencies have started to apply for bug bounty programs whereby they can invite independent ethical researchers from worldwide to test the security of their systems and applications and provide information on any required fixes.
The most famous examples of bug bounty programs launched by government sector agencies are the “Hack the Pentagon” program initiated by the U.S. Department of Defense, the Security Vulnerability disclosure program by Bundeswehr (German Armed Forces), the bug bounty program by Swiss Post, and others. At the same time, a government may also establish state-backed bug bounty platforms such as the ones operating in Kazakhstan and Saudi Arabia. For government agencies, the ultimate security of citizens’ data is a top priority. The fact that they trust ethical researchers is the confirmation of high ethical standards followed by bug bounty platforms such as HackenProof.
One of the most recent examples of launching a bug bounty program by a government sector agency has taken place in Ukraine. At the end of July 2021, the Ministry of Digital Transformation of Ukraine has decided to launch a bug bounty program to test the security of the application Diia, the state online services portal. The total prize pool of this bug bounty program is 1 mln UAH ($35,000). This case is of the greatest interest to the global cybersecurity community. Ukraine has become one of the fastest-growing countries in terms of the pace of digital transformation. Namely, it has been the first country in the world to fully legalize digital passports and one of the global pioneers in the adoption of blockchain technologies. That is why, based on the information provided above, it’s reasonable to suggest that cooperation between government sector agencies and independent researchers through the mechanism of bug bounty programs is likely to become the future of cybersecurity in both developed and developing countries.
Bug bounty programs: mechanism and advantages for government
The bug bounty program is a security testing process whereby independent ethical researchers either registered on specialized platforms or invited by a company ordering such services can work on detecting security weaknesses in its products and systems in exchange for financial rewards and recognition. Bug bounty programs do not substitute other forms of security testing but rather should be implemented in parallel with them. The entity applying for running a bug bounty program specifies its terms and conditions and the sum of rewards to be paid to ethical researchers for revealed bugs. For more information about bug bounty programs, their duration, and difference from other forms of security testing, please refer to the following article.
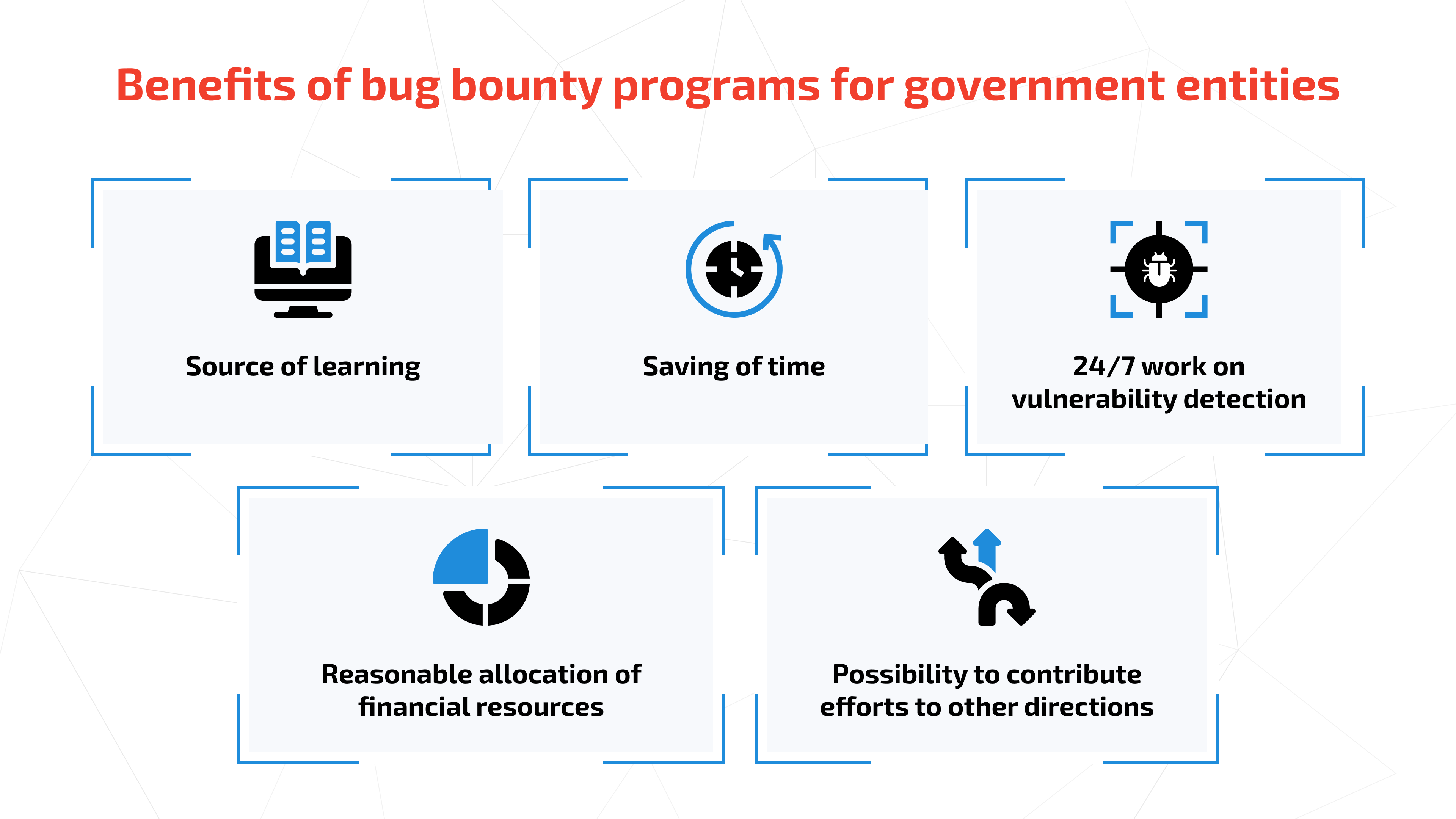
Governments are interested in running bug bounty programs since this form of security testing allows them to achieve the desired high-quality outcomes in a fast and financially efficient way. Instead of maintaining a huge internal staff of high-paid cybersecurity specialists, a government, when required, organizes a bug bounty program and pays to ethical researchers only for revealed bugs, non-required expenditures are not related to bug bounty programs. At the same time, reputable bug bounty platforms are interested in cooperating only with highly professional ethical researchers and that is why governments applying for bug bounty programs face minimal security and disclosure risks.
HackenProof: reliable bug bounty platform for government entities
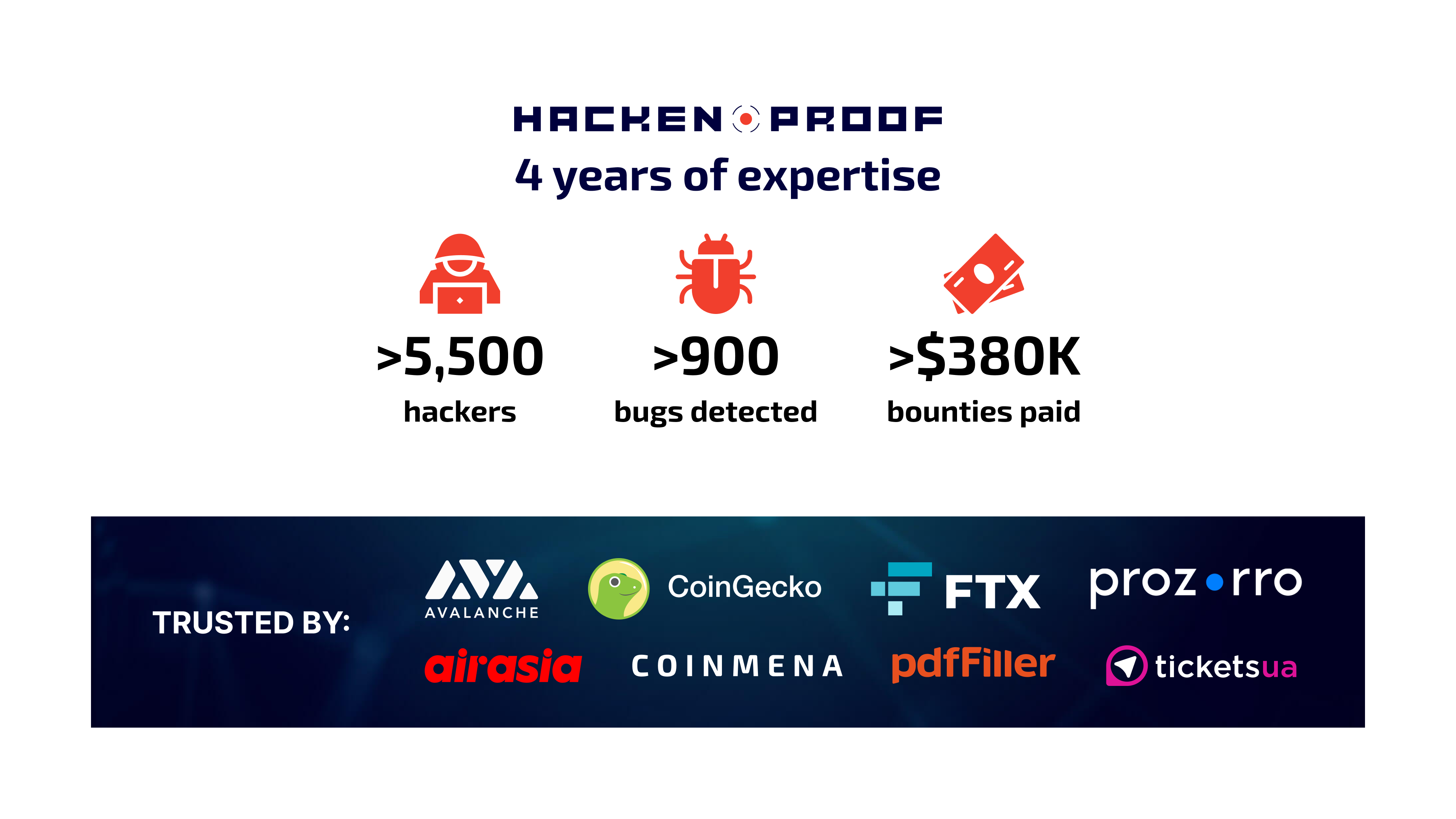
HackenProof is one of the leading European bug bounty platforms that has been serving the security needs of private and public companies since 2017. The list of entities that have cooperated with HackenProof includes such brands as Kuna, CoinGecko, Prozorro, Gate.io, and others. HackenProof is the core element of the Hacken ecosystem of cybersecurity projects. Hacken professionalism in cybersecurity and high ethical standards have been recognized by the Ministry of Digital Transformation of Ukraine in the form of a Memorandum of cooperation signed between the two parties in December 2020. The recognition by the Ministry is a great confirmation of the fact that HackenProof is a reliable cybersecurity vendor for the entities interested in mitigating any security risks when testing their products.
HackenProof’s competitive advantages over other vendors are attractive subscription plans, reliable community, and constant improvement. HackenProof’s core team is focused on facilitating client’s experience. For example, one of the recent updates has been related to the application process. Now clients can apply for running a bug bounty program even without the need to contact our team, full autonomy. Of course, you can always reach our specialists in case you need some assistance during the registration process. You can find more information about HackenProof, our partners, and key figures in this material.
How to start working with HackenProof?
As mentioned above, entities can apply for running a bug bounty program on HackenProof even without the involvement of our support team, just by filling in the required information in the application form. In case you are not sure what information you need to provide, you are free to contact our team through the chatbot on our website as well as on social media. Our team will reply to your requests ASAP.
HackenProof Website: https://hackenproof.com/
HackenProof Facebook: https://www.facebook.com/hackenproof/
HackenProof Twitter: https://twitter.com/hackenproof
HackenProof Telegram: https://t.me/hackenproof
HackenProof Instagram: https://www.instagram.com/hackenproof/

