Brazil has always been one of those countries where cybersecurity issues are hard to report. Back in September, we have already reported a big leak by a Brazilian online booking system exposing personal data of almost 500,000 people. The company behind the exposure was really hard to identify and contact, but at the end of the day, the database was secured mainly due to our Twitter followers support.
On November 12th, when auditing the search results for open/exposed Elasticsearch databases with Binaryedge.io platform, we have found what appeared to be a collection of personal records compiled by FIESP, the Federation of Industries of the State of São Paulo. FIESP is the largest class entity in the Brazilian industry. It represents about 130 thousand industries in various sectors, of all sizes and different production chains, distributed in 131 employers’ unions.
Records were stored in Elasticsearch with the total count of 180,104,892.
At least 3 indices (FIESP, celurares and externo) that we have analyzed contained the personal info of Brazilian citizens.
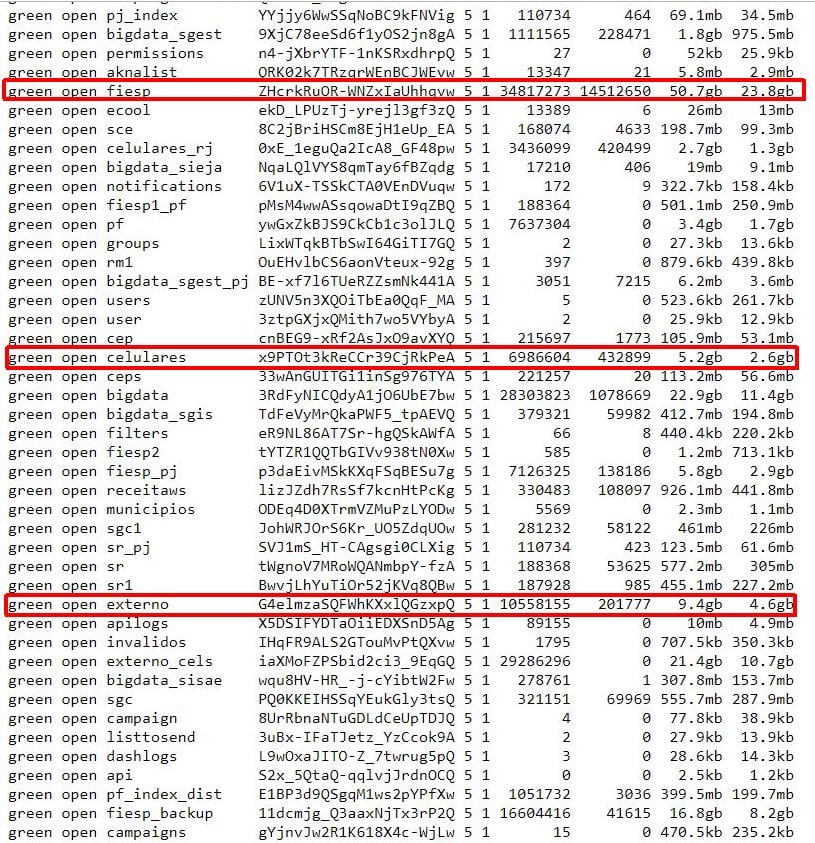
The largest collection of data (FIESP collection) had 34,817,273 personal records with exposed info like:
- name
- personal ID number (RG number)
- taxpayer registry identification (CPF)
- sex
- date of birth
- full address
- phone number
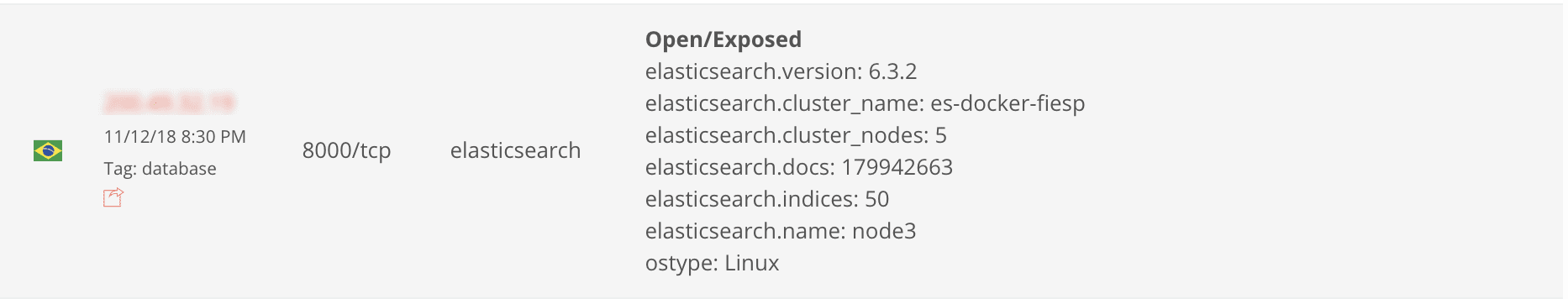
We have immediately sent notifications to FIESP contacts but never received any response. The database was taken offline only after our Brazilian-based follower, Paulo Brito, managed to get in touch with a FIESP representative over the phone and inform them about the exposure.
This article will be updated if/when we hear back from FIESP as of steps taken to protect this sensitive data.
DANGER OF OPEN ELASTICSEARCH INSTANCES
We have previously reported that the lack of authentication allowed the installation of malware or ransomware on the Elasticsearch servers. The public configuration allows the possibility of cybercriminals to manage the whole system with full administrative privileges. Once the malware is in place criminals could remotely access the server resources and even launch a code execution to steal or completely destroy any saved data the server contains.
Please take note, that we regularly publish reports on data leaks. For example, we’ve recently written about kars4kids data leak.
To learn on how you can minimize the risks of your cloud infrastructure becoming exposed – contact us for a free consult

